🛰️ How to Convert a Smoothtalker Directional Antenna into a Full-Spectrum RF Threat Detector Why You Only Need One Well-Modified Antenna — Not a $40,000 TSCM Kit 📡 Why This Antenna? The Smoothtalker SEMUDA2XL Arrow MCT antenna is a directional log-periodic-style antenna originally designed for cellular band signal boosting (600 MHz–6 GHz).But with the right modifications, it
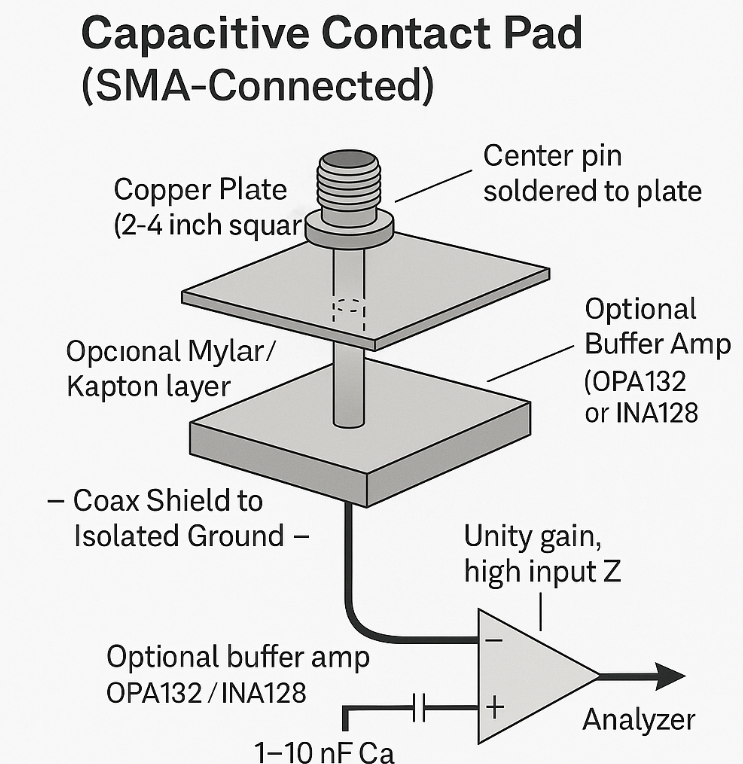
🔌 Build a Capacitive Contact Pad for Covert Signal Detection ⚠️ Warning: Don’t Connect Raw Pads Directly to Your Analyzer ❌ Never connect a raw contact pad (like an EEG electrode or copper plate) directly to the BB60C or any spectrum analyzer.✅ These sensors can carry DC bias, high impedance, and even static discharge that
🛰️ The Multilayered Antenna System How to Detect the Undetectable — Even When No Single Antenna Can 🧠 Short answer: ❌ No — there is no “perfect” antenna that no signal can evade.✅ But a multilayered antenna system, paired with the right signal analysis tools, can make evasion functionally impossible. Covert transmitters, implants, and LPI
🧠 Can Narrowband Signals Trigger the Frey Effect? Why a Single Tone Fails, but a Coherent RF Comb Can Succeed The Frey effect, also known as the microwave auditory effect, is real and scientifically documented. It allows a human to perceive sound through pulsed microwave radiation—without using the ears. But there’s a widespread misconception in
🎯 Can These Techniques Evade a Log-Periodic Antenna Pointed Up (Omni-Like Orientation)? 🔧 Setup: 🧠 Short Answer: ✅ Yes — many of these covert techniques can evade detection in that configuration, depending on the signal geometry, polarization, and field type. Let’s walk through each technique and how it behaves with a log-periodic antenna pointed up:
🧠 How to Detect Covert Signals Without Missing Them — A Technical Guide Covert signals are often engineered to avoid your tools — not physics. You won’t miss them because your antenna fails; you’ll miss them because your process isn’t designed to catch what they’re doing. Below are detailed methods to capture and reveal even
🛰️ Why Antennas Don’t Lie — But Signals Can Still Evade Detection 📡 According to fundamental RF theory and TSCM training: If a signal is radiating within the spatial range and frequency band of an antenna, the antenna will receive it. This is electromagnetics 101 — every radiated electromagnetic wave within the antenna’s pattern induces
🎯 Why Some Signals Are Practically Undetectable — Even with the Signal Hound BB60C 🛰️ In the search for proof of directed energy and neurological interference technologies, tools like the Signal Hound BB60C are essential. But even this high-performance spectrum analyzer has limitations — and covert signal designers know exactly how to work around them.
🎯 Exposing Covert Signals: How to Analyze Sub-Hertz Frequencies with IQ Data from the BB60C 🛰️ New Discovery Tool: Covert signals can now be analyzed down to 0.001 Hz resolution bandwidth (RBW) — allowing us to detect ultra-narrow, biologically reactive, and obfuscated RF threats that were previously invisible to normal scans. This blog post shows
How to Reveal Hidden Signals Below the Noise Floor 🧠 Most covert threats aren’t loud. They’re quiet, subtle, and designed to hide—not just from ordinary scanners, but from trained professionals using standard settings. That’s why we’re introducing a proven, field-tested method to reveal these threats: “The Noise Floor Sweep Differential Technique.” With just two waterfall