🧠 The Brain as the New Battlefield: Dr. James Giordano’s Terrifying Warning Becomes Reality 📍 Originally presented at Georgetown University, Dr. James Giordano’s now-infamous lecture outlined the future of warfare — a future dominated not by bullets and bombs, but by neurons, nanotech, and neuro-cognitive hacking. What sounded like science fiction in the early 2010s
📚 Table of Contents 🎯 Overview for Targeted Individuals (TIs) This report, based on a detailed transcript of a Blaze News video featuring Steve Baker and Katherine Herridge, confirms everything many TIs have experienced for years: 👉 For the TI community, this is not a revelation — it’s long-awaited recognition. 🏛️ 1. Congressional Acknowledgement (May
📡 FCC Database Lookup Script – Help Us Map the Airwaves Are you tired of blindly guessing who’s broadcasting on a frequency? Our new open-source script is built to upload and process FCC licensing data into a PostgreSQL database — allowing you to correlate start and stop frequencies from a CSV file with the actual
🛰️ How to Convert a Smoothtalker Directional Antenna into a Full-Spectrum RF Threat Detector Why You Only Need One Well-Modified Antenna — Not a $40,000 TSCM Kit 📡 Why This Antenna? The Smoothtalker SEMUDA2XL Arrow MCT antenna is a directional log-periodic-style antenna originally designed for cellular band signal boosting (600 MHz–6 GHz).But with the right modifications, it
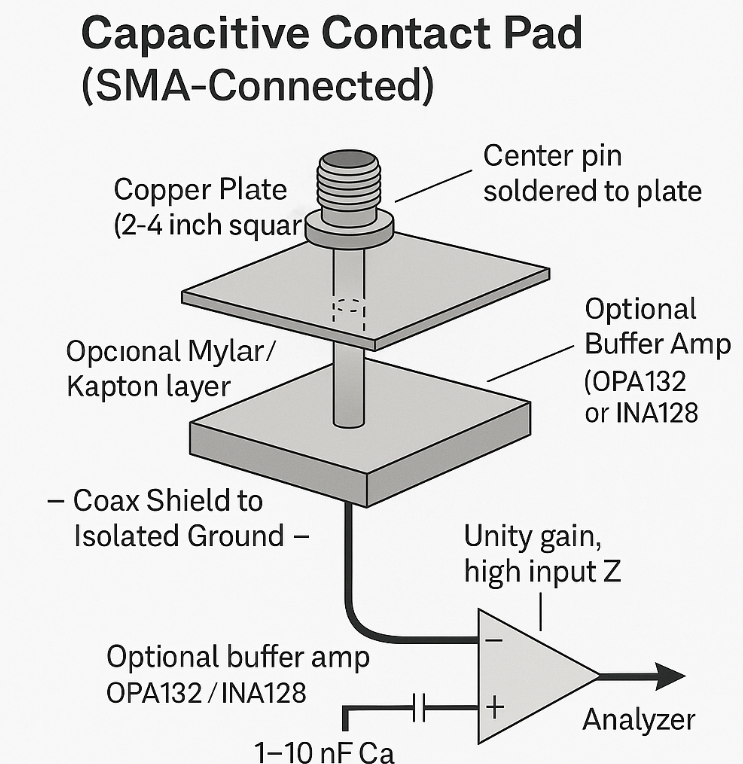
🔌 Build a Capacitive Contact Pad for Covert Signal Detection ⚠️ Warning: Don’t Connect Raw Pads Directly to Your Analyzer ❌ Never connect a raw contact pad (like an EEG electrode or copper plate) directly to the BB60C or any spectrum analyzer.✅ These sensors can carry DC bias, high impedance, and even static discharge that
🛰️ The Multilayered Antenna System How to Detect the Undetectable — Even When No Single Antenna Can 🧠 Short answer: ❌ No — there is no “perfect” antenna that no signal can evade.✅ But a multilayered antenna system, paired with the right signal analysis tools, can make evasion functionally impossible. Covert transmitters, implants, and LPI
🧠 Can Narrowband Signals Trigger the Frey Effect? Why a Single Tone Fails, but a Coherent RF Comb Can Succeed The Frey effect, also known as the microwave auditory effect, is real and scientifically documented. It allows a human to perceive sound through pulsed microwave radiation—without using the ears. But there’s a widespread misconception in
🎯 Can These Techniques Evade a Log-Periodic Antenna Pointed Up (Omni-Like Orientation)? 🔧 Setup: 🧠 Short Answer: ✅ Yes — many of these covert techniques can evade detection in that configuration, depending on the signal geometry, polarization, and field type. Let’s walk through each technique and how it behaves with a log-periodic antenna pointed up:
🧠 How to Detect Covert Signals Without Missing Them — A Technical Guide Covert signals are often engineered to avoid your tools — not physics. You won’t miss them because your antenna fails; you’ll miss them because your process isn’t designed to catch what they’re doing. Below are detailed methods to capture and reveal even
🛰️ Why Antennas Don’t Lie — But Signals Can Still Evade Detection 📡 According to fundamental RF theory and TSCM training: If a signal is radiating within the spatial range and frequency band of an antenna, the antenna will receive it. This is electromagnetics 101 — every radiated electromagnetic wave within the antenna’s pattern induces