📄 Introduction In a compelling submission to the United Nations Office of the High Commissioner for Human Rights (OHCHR), a self-identified Targeted Individual (TI) from India details experiences of covert torture using advanced military-grade technologies. This document, titled “Inputs for psychosocial dynamics conducive to torture and ill-treatment,” sheds light on the alleged use of remote
Remote Mind Control Technology: An Archived Scientific Investigation into EMF-Based Neural Influence
🔍 Introduction This blog post presents a detailed investigation into a rare and often-overlooked document titled “Remote Mind Control Technology” by Anna Keeler, originally published in MindNet Journal, Vol. 1, No. 23a. The article is publicly available via the Internet Archive: 🔗 Anna Keeler – Remote Mind Control Technology (Archive.org) The content outlines the use
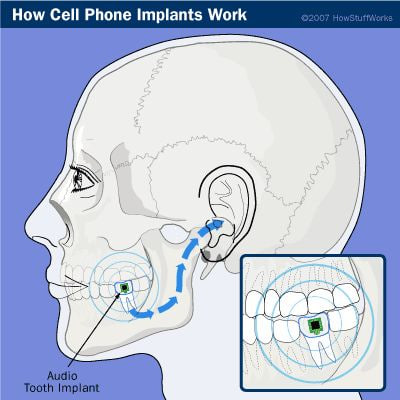
🔍 Overview In 2001, designers James Auger and Jimmy Loizeau introduced the world to the Audio Tooth Implant, a pioneering concept in personal communication technology. This innovative idea envisioned a miniature audio output device and receiver implanted into a tooth, allowing users to receive audio information directly through bone conduction. The project aimed to explore
🔍 Overview In 2009, a shocking webpage archived on Lightning GPS’s official website marketed a product called Bio-Track: an alleged implantable and swallowable GPS tracking device developed by a German R&D firm named Voss-Mauser. The claims on this page were extraordinary—and disturbing. The Bio-Track was described as a globally-deployed covert tracking device with sci-fi features
🧲 Everything Around You Emits EMF — And This Video Proves It If you’re a Targeted Individual (TI) trying to prove you’re being attacked with electromagnetic fields (EMFs), you’ve probably already tried using an EMF meter — and likely been disappointed. You might feel symptoms, but your meter reads “safe.” So what gives? The truth
📡 Taking Pictures of Frequencies: How Targeted Individuals Can Capture Evidence Using Project COGSWORTH and the BB60C If you’re a Targeted Individual (TI) enduring remote neural monitoring (RNM), synthetic telepathy, or electromagnetic harassment, the hardest part is proving it. These attacks leave no bruises, no paper trail — only symptoms. But the truth is: the
Level 1 – Everyday Consumer Devices and Playthings Equipment Needed: Threats Detected: Level 2 – Basic Consumer and Commercial Devices Equipment Needed: Threats Detected: Level 3 – Advanced Consumer and Commercial Devices Equipment Needed: Threats Detected: Level 4 – Semi-Professional and Covert Surveillance Devices Equipment Needed: Threats Detected: Level 5 – Professional and Government Surveillance
In the realm of Technical Surveillance Countermeasures (TSCM), comprehending the significance of Signal of Interest (SOI) and the Fundamental Frequency is crucial for effectively identifying and mitigating security threats. This page will delve into these concepts and their detection methods in detail, including the utilization of signal intelligence software for verification and comparative analysis. Signal
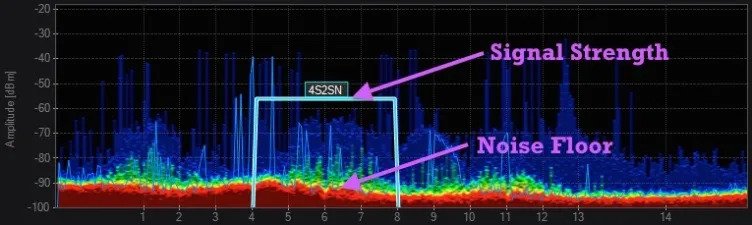
In the world of electronic surveillance and countermeasures, precision and sensitivity are paramount. Whether you are concerned about corporate espionage, government surveillance, or protecting sensitive information, it’s crucial to understand the significance of having a noise floor at -172 dB. In this guide, we’ll delve into why this level of sensitivity is essential and why
The top SOI is found at 1.33ghz center frequency. It was found using a BB60C spectrum analyzer in a shielded environment. The environment was shielded with Y-Shield HSF54 and nickel and copper curtains. By shielding the room it reduced the frequency list significantly. Taking the list down from well over 6,000 frequencies to classify to