Understanding SOI (Signal of Interest) and Fundamental Frequency in TSCM
In the realm of Technical Surveillance Countermeasures (TSCM), comprehending the significance of Signal of Interest (SOI) and the Fundamental Frequency is crucial for effectively identifying and mitigating security threats. This page will delve into these concepts and their detection methods in detail, including the utilization of signal intelligence software for verification and comparative analysis.
Signal of Interest (SOI)
Defining SOI: A Signal of Interest (SOI) is any frequency or electromagnetic signal that raises suspicion due to its distinctiveness in comparison to the ambient background radiation. In the context of TSCM, SOIs are potential indicators of unauthorized surveillance devices or eavesdropping equipment, presenting a potential security threat.
Detecting SOIs: TSCM specialists employ various techniques to detect SOIs, including time-based and location-based differentials, signal intelligence software, and comparative analysis.
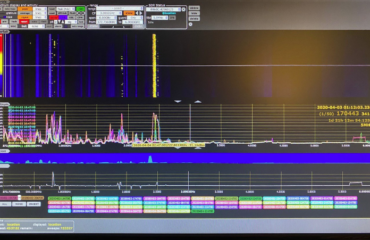
- Time-Based Differential: This approach involves using a Fast Fourier Transform (FFT) to analyze signals over different time frames. Each time frame is represented in a different color on the FFT plot, allowing for the comparison of frequency patterns. Unusual frequencies that appear in one timeframe but not in others may be identified as SOIs.
- Location-Based Differential: TSCM professionals perform sweeps in multiple locations using similar FFT setups. Each location’s FFT plot is compared, and discrepancies in detected frequencies between locations can reveal potential SOIs.
- Signal Intelligence Software: Specialized software applications such as Krypto 500 or Krypto 1000 are invaluable tools in TSCM. These software packages provide advanced signal analysis capabilities, allowing experts to identify SOIs by comparing detected signals to known signatures, demodulating signals for content analysis, and precisely determining the fundamental frequency.
- Comparative Analysis: TSCM experts may also employ comparative analysis techniques, such as comparing FFT and Waterfall plots, to known frequency patterns from their training or established references like Signal ID Wiki. This method aids in identifying the fundamental frequency with greater precision.
Importance of SOI Detection: The detection of SOIs is a crucial aspect of TSCM, serving as an early warning system for potential security breaches. Identifying these signals allows specialists to locate and address security threats promptly, safeguarding sensitive information and maintaining confidentiality.
Fundamental Frequency
Understanding the Fundamental Frequency: The Fundamental Frequency, often referred to as the “fundamental,” represents the primary frequency component of a signal. In TSCM, it corresponds to the actual attack frequency— the frequency at which eavesdropping devices transmit data or audio.
Verifying the Fundamental Frequency: TSCM experts use various methods to verify the fundamental frequency, including comparative analysis and signal intelligence software.
- Physical Identification: The presence of eavesdropping equipment can provide direct evidence of the fundamental frequency. TSCM professionals may identify and physically inspect the offending equipment to determine the exact frequency.
- Demodulation: In cases where demodulation is possible, specialists can extract audio or video data from a bug. The frequency at which this data is extracted is considered the fundamental frequency.
- Signal Intelligence Software: Specialized software applications like Krypto 500 or Krypto 1000 can assist in precisely identifying the fundamental frequency by analyzing signal characteristics and comparing them to known signatures.
- Comparative Analysis: Comparative analysis of known frequency patterns and detected signals can aid in pinpointing the fundamental frequency with precision.
Recording IQ Data: It remains imperative to record IQ (In-Phase and Quadrature) data immediately upon identifying the fundamental frequency, especially when employing signal intelligence software or conducting comparative analysis. This data serves as essential evidence, aiding further analysis and potential legal action.
In summary, SOIs are suspicious frequencies detected through various methods, including the use of signal intelligence software and comparative analysis. The Fundamental Frequency represents the attack frequency identified from a SOI list and can be verified through physical identification, demodulation, signal intelligence software, and comparative analysis. Recording IQ data is crucial for preserving evidence. Understanding and effectively identifying SOIs and their fundamental frequencies are essential for TSCM specialists to proactively respond to potential security threats, ensuring the protection of sensitive information and maintaining security and confidentiality.