🛰️ FULL TELEMETRY INDEX FOR HUMAN/BODY TRACKING IN SIGINT 🔴 1. Active Emissions (Direct RF sources from/on the target) Type Description Detectability GPS/GNSS metadata Raw satellite pings from smartphones, trackers, cars Easy (if unencrypted) Wi-Fi MAC pings Probe requests broadcast by phones looking for networks Medium Bluetooth BLE beacons Constant presence signals from smartwatches, earbuds,
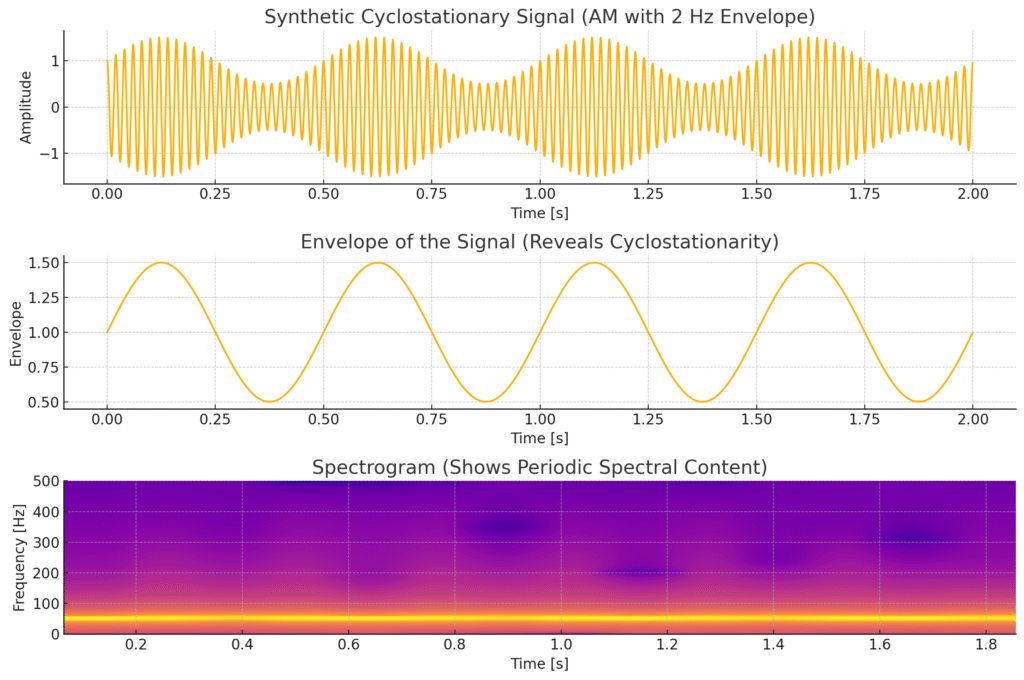
🧠 Cyclostationary Analysis in Signal Intelligence: A TI-Friendly Tutorial 🔍 What Is Cyclostationary Analysis? Cyclostationary analysis is a powerful tool in signal intelligence (SIGINT) used to detect and classify repetitive, structured patterns in electromagnetic signals, especially those designed to hide in noisy environments. Unlike a basic spectrum analyzer — which only shows how much energy
Tooth Inspection of 1.33 GHz Comb: Signal Analysis and Interpretation Tools Used: Signal Hound BB60C, FFT Spectrogram, IQ Analysis Software 🔍 Overview During spectral surveillance using a Signal Hound BB60C analyzer, a highly structured signal was observed within the 1.327 to 1.334 GHz band. This band is largely unoccupied by public commercial applications, making anomalies
🎯 Real-Time Signal Detection with BB60C and CSV Export for FCC Lookup 📡 In the world of RF surveillance, detecting low-SNR or ultra-wideband (UWB) signals is like finding a needle in a haystack—especially when those signals might only appear briefly or blend into the noise floor. That’s where this custom Python script comes in. This
🧠 How to Detect Covert Signals Without Missing Them — A Technical Guide Covert signals are often engineered to avoid your tools — not physics. You won’t miss them because your antenna fails; you’ll miss them because your process isn’t designed to catch what they’re doing. Below are detailed methods to capture and reveal even
🛰️ Why Antennas Don’t Lie — But Signals Can Still Evade Detection 📡 According to fundamental RF theory and TSCM training: If a signal is radiating within the spatial range and frequency band of an antenna, the antenna will receive it. This is electromagnetics 101 — every radiated electromagnetic wave within the antenna’s pattern induces
🎯 Why Some Signals Are Practically Undetectable — Even with the Signal Hound BB60C 🛰️ In the search for proof of directed energy and neurological interference technologies, tools like the Signal Hound BB60C are essential. But even this high-performance spectrum analyzer has limitations — and covert signal designers know exactly how to work around them.
How to Reveal Hidden Signals Below the Noise Floor 🧠 Most covert threats aren’t loud. They’re quiet, subtle, and designed to hide—not just from ordinary scanners, but from trained professionals using standard settings. That’s why we’re introducing a proven, field-tested method to reveal these threats: “The Noise Floor Sweep Differential Technique.” With just two waterfall
Advanced Guide: Beamforming with Split Comb Frequencies & Gaussian Modulation 🎛️ Overview of the Technique This method employs a highly precise form of beamforming using a comb frequency, split into two sub-combs, each modulated with a Gaussian power envelope. This technology focuses electromagnetic energy onto a single, specific target location, significantly reducing unintended exposure and
🛰️ Understanding Low Probability of Intercept (LPI) Radar: Stealthy Detection Technology Imagine you’re a 🕵️ detective in a high-stakes game of cat and mouse, trying to spot a suspect without them knowing you’re watching. In the military world, this is the essence of Low Probability of Intercept (LPI) radar — a technology designed to detect
- 1
- 2