Advanced Guide: Beamforming with Split Comb Frequencies & Gaussian Modulation 🎛️ Overview of the Technique This method employs a highly precise form of beamforming using a comb frequency, split into two sub-combs, each modulated with a Gaussian power envelope. This technology focuses electromagnetic energy onto a single, specific target location, significantly reducing unintended exposure and
📡 Why Real Threat Detection Takes 6+ Months of 24/7 Monitoring 🧠 Overview Finding and documenting a true covert threat — especially RF-based threats like Voice-to-Skull (V2K), directed energy, or remote neural monitoring — is not a quick process.It requires months of non-stop, high-resolution surveillance with professional-grade tools. This isn’t just theory — it’s the
🚁 Focused Ultrasound Jamming Collar: 40kHz vs 300kHz Deep Analysis for TI Countermeasures 🔊 Introduction The idea of using a Focused Ultrasound Jamming Collar to disrupt hypothetical subvocal implants has gained attention in the TI (Targeted Individual) community. This concept is rooted in both real military research and speculative technology. Recent research suggests that 300
🧠 How to Build a V2K Resonant Frequency Detector with Vibration Sensors Capture the 1.33 GHz comb signal resonating on your body — and record the proof. ⚙️ Overview This device isn’t a normal SDR or spectrum analyzer. It’s a resonance-coupled, field-based sensor that detects microwave signals resonating on or in your body — specifically
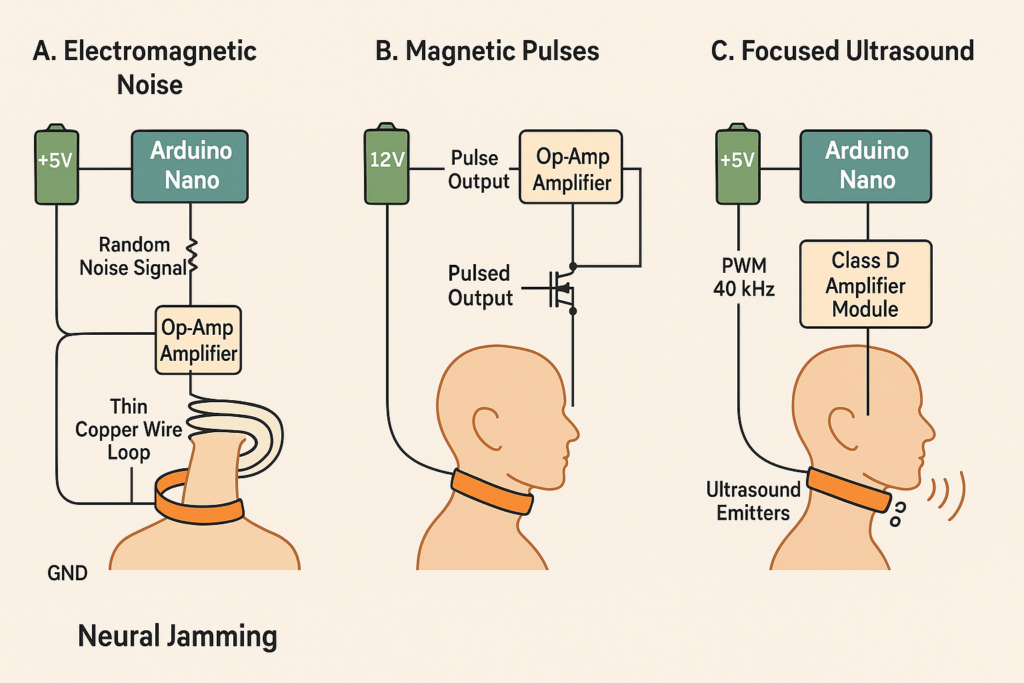
🛡️ How to Jam Subvocal Implants: 3 Realistic TI Countermeasure Methods 🌌 Introduction With official programs like the U.S. Army’s 2019 “Neural Enhancement & Jamming Countermeasures” confirming the viability of neural disruption, it’s time to bring real DIY countermeasures into the hands of Targeted Individuals (TIs). 💥 Below are 3 powerful methods you can build
🌌 How Subvocal Implants Stay Powered: A Deep Dive into Energy Sources and Disruption Methods Subvocal communication implants, like those rumored from DARPA’s “Silent Talk” project, are fascinating feats of engineering. Some are alleged to operate for 10+ years without traditional batteries, possibly using retro-reflector methods. Let’s explore every possible way these implants might stay
📡 Why HackRF and RTL-SDR Are Not Suitable for Serious Security Work 🎯 When conducting advanced RF security analysis, it’s critical to select appropriate, high-quality equipment. Devices like HackRF and RTL-SDR, although popular among hobbyists and beginners, are not adequate for professional-grade security tasks. 🚨 Their persistent use in the security community promotes a dangerous