🧠📡 Synthetic Telepathy & Signal Intelligence Toolkit A New Forensic Framework for Covert Signal Detection and Brainwave Correlation Are you being targeted by directed energy weapons, strange bursts of RF signals, or suspected synthetic telepathy attacks? Most technical surveillance countermeasure (TSCM) tools stop short — identifying “signals of interest” without proof or correlation. That’s why
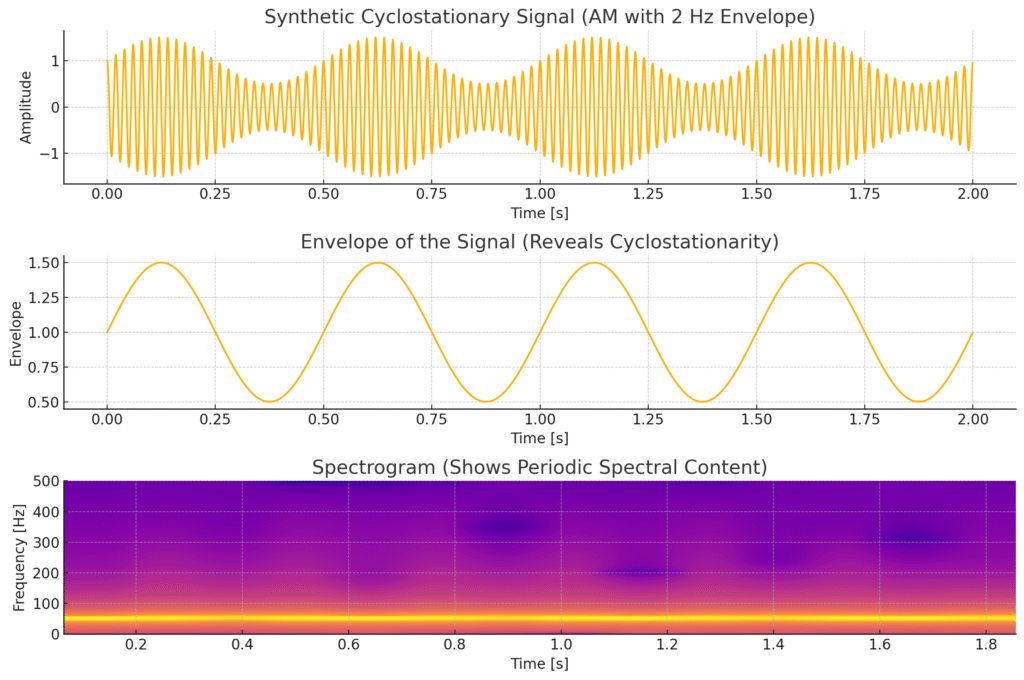
🧠 Cyclostationary Analysis in Signal Intelligence: A TI-Friendly Tutorial 🔍 What Is Cyclostationary Analysis? Cyclostationary analysis is a powerful tool in signal intelligence (SIGINT) used to detect and classify repetitive, structured patterns in electromagnetic signals, especially those designed to hide in noisy environments. Unlike a basic spectrum analyzer — which only shows how much energy
❌ Why 95% of TSCM Experts Can’t Generate a Real Report for Targeted Individuals (TIs) In the world of TSCM (Technical Surveillance Countermeasures), most professionals are trained to sweep for commercial bugs—GSM microphones, hidden cameras, wireless transmitters. But when a targeted individual (TI) requests help, 95% of TSCM personnel fall short. Not due to lack
🚫 Why REI’s TSCM Training Falls Short Against State-Level Threats In the world of Technical Surveillance Countermeasures (TSCM), REI (Research Electronics International) is a popular name, especially among corporate security teams and entry-level sweep technicians. Their training programs and flagship tool—the OSCOR spectrum analyzer—are widely promoted as industry standards. But here’s the hard truth: REI’s
🛡️ How to Build a Radar-Absorbing Coating to Shield Your Home from Surveillance and Attacks Radar powers military surveillance, synthetic aperture imaging, and even directed-energy weapons. This guide walks you through creating a radar-absorbing material (RAM) coating to make your home nearly invisible to radar-based threats across 1–40 GHz. Using real electromagnetic science, this coating
🧠 How to Vet a Technology, Scan, or Service: A Critical Thinking Checklist In the targeted individual (TI) space, where confusion and technical deception are common, it is essential to properly evaluate whether a product, scan, or service is legitimate or fraudulent. This guide includes a step-by-step checklist and AI-based prompts to help you make
⚖️ New Resource: Legal Demand Letter Template for Victims of Fraud We are excited to release the Legal Demand Letter Template as part of the Legal Action Toolkit for the targeted individual (TI) community. This resource is designed to help you take real, actionable steps toward holding fraudulent actors accountable — without needing a lawyer.
🔍 Introducing the Scam Report Archive: A Permanent Record of Truth In an effort to bring lasting transparency and accountability to the targeted individual (TI) community, we are proud to announce the launch of the Scam Report Archive — a living record of fraud exposure, failed scan technologies, and discredited service providers. This new section
📄 Fraud Reporting Documentation Toolkit This toolkit provides ready-to-use templates and forms for reporting individuals, organizations, or groups who promote, sell, or manufacture fraudulent products or services within the Targeted Individual (TI) community. These resources are designed to empower victims and concerned citizens to take action through legitimate legal and regulatory channels. 🧾 1. Complaint
🚨 Legal Implications for Promoting Scam Products and Reports In the targeted individual (TI) community, we’ve seen repeated instances where groups promote fraudulent products, fake scan reports, and deceptive technologies. Even if these groups do not directly sell these items, they can still face legal liabilities. ⚖️ Legal Accountability Under U.S. law and similar legal