
Survival Guide
🛡️ Targeted Individual Survival Guide: What Still Works and What to Rethink
This guide was originally circulated in 2020. While some advice remains useful, technology and tactics have evolved, and some items may be outdated or even counterproductive. Below is an updated, critically reviewed version—organized for clarity, safety, and practical use.
🚨 Harassment Tactics to Expect
- Financial Sabotage: Harassers often try to induce panic so you’ll make irrational decisions like quitting jobs or moving repeatedly. Staying grounded and documenting evidence is key.
- Isolation: Isolation amplifies the attack. Understand the tactics used (e.g. disinformation, voice-to-skull) and resist by staying in touch with a trusted support network.
- Remote Neural Monitoring Claims: While claims of implants like throat or dental devices persist, they remain controversial. If suspected, see our blog post on imaging implants with ultrasound and other methods.
- Psychological Entrapment: These tactics aim to provoke behavior that leads to arrest, psychiatric commitment, or self-harm. Maintain composure. Avoid retaliation. Document everything.
- Forced Institutionalization: Don’t give ammunition for mental health accusations. Stay composed and never claim unverifiable information to police or doctors.
🧠 Psychological Defense
- Don’t Overshare with Non-TIs: Talking about targeting to unaware friends/family can lead to social isolation or worse—mental health flags.
- Don’t Go to Police or Psychologists Unprepared: If needed, consult a civil rights attorney first. Talking about implants or voices without strong evidence may lead to commitment.
- Invoke Your Rights: If questioned about targeting or firearms by law enforcement, say “talk to my lawyer.” This invokes your Fifth Amendment protection.
- Avoid High-Density Housing: If shielding is your concern, detached living spaces are best. RV parks are a budget solution, but modern shielding strategies may work in apartments.
- Surveillance Deterrents: Bodycams, wired security cameras, and documentation reduce street theater activity.
🔐 Who to Trust (With Caution)
- Limited Trust Circle: Trust family only if they’ve proven safe. Romantic partners can be honeytraps. Remote anchoring (voice spoofing) is real—trust your gut, not the voice in your head.
- Don’t Trust Voices or V2K Content: 90% of voice-to-skull (V2K) messages are disinformation or AI chatterbots.
- Never React with Violence or Illegality: It gives them the outcome they want.
🖥️ Digital Security
- Devices Are Compromised: Assume your phone, computer, and smart TV are compromised. Use Linux-based systems, monitor network activity, and consider physical modifications.
- Dental Surveillance Risk: Suspicious dental work? Research alternatives, and document all procedures. Avoid blind trust in dentists—especially with molar implants.
- Don’t Travel Internationally: Varying laws may increase your risk abroad.
- Avoid Remote Camps: Isolated areas are high-risk for staged abduction or implantation.
- Court Wins Don’t End the Program: Implants and remote influence may continue even after legal victories.
🏠 Physical Security Upgrades
- Recommended Security Tools:
- Electric fencing (if legal)
- Wired cameras (not WiFi)
- Battery-backed alarms
- Motion detectors
- Protection dogs
- Hardened entry points (brick walls, steel doors, RF seals)
- Backup Evidence: Use encrypted USB drives, multiple off-site copies, and cloud storage with zero-knowledge encryption (e.g., Proton Drive).
- Keep Critical Tools with You: Bring your laptop, USB backups, and counter-surveillance gear when moving.
- Avoid Desktop PCs: Use hardened laptops with removable batteries and Ethernet-only connections.
- Use PF Sense Firewalls: Routers flashed with PF Sense gives intrusion detection give more control. PF Blocker and Snort are a must.
- Don’t Use WiFi: Always go wired. Block RF leakage with shielding materials.
- Hardware Hardening: Disable microphones and cameras physically. Use external mic-only headsets when absolutely necessary.
- Use Software Like FourShadow: It’s designed to detect unauthorized system changes and anomalies.
🕵️ Social and Situational Awareness
- Beware Double Agents in TI Groups: Some people claiming to be TIs are actually informants. Be discreet.
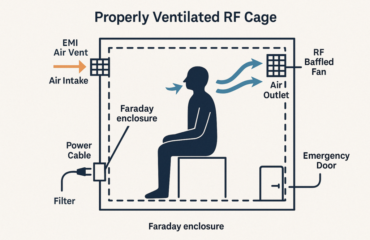
- Shield Your Environment: Build a faraday cage or shielded room (1 Hz – 100 GHz) using copper, steel, or mu-metal. Include RF-sealed doors and vents.
- Avoid Gimmick Devices: Qwave and other commercial “anti-targeting” devices are often scams.
- Magnets Don’t Block Targeting Tech: Even a 75 lb magnet won’t stop RF, scalar, or acoustic weapons.
- Avoid Sensitive Conversations Over Calls: Assume all calls are monitored.
- Watch Out for Scams: Be cautious of anyone selling anti-harassment tech or asking you to sign away rights.
- They Can Jam Scanning Tools: RF implants may include jamming to avoid detection. Scan multiple times with different gear.
- Most V2K is AI-Controlled: It’s a bot designed to engage, harass, and extract information.
- Fill Out a TI Affidavit: Useful for legal documentation if you’re pursuing a case.
- Watch for Holograms: Projectors pointed at holographic foil can simulate alien/snake imagery. This is a known scare tactic.
- 3 Types of V2K to Know:
- Harassment (insults, threats)
- Remote Influencing (planted thoughts)
- Remote Anchoring (voice imitation of family/friends)
🧠 Final Thought
Survival for TIs is a mix of tech, strategy, and mental resilience. Use logic, avoid fear traps, and document everything. Not all guidance stands the test of time—but adapting, staying calm, and protecting yourself does.

I have been a victim of of v2k and gang stalking for 16 years just figured out what it is and I need help in understanding